What if your private 5G network, heralded as a beacon of innovation and efficiency, inadvertently becomes your biggest operational risk—rather than your strongest asset?
The promise of private 5G and LTE networks is undeniable. They are the backbone for the next generation of industrial automation, critical infrastructure development, and the creation of smart, interconnected campuses. From manufacturing plants and logistics hubs to airports and utilities, these networks are driving Industry 4.0 transformation, enabling real-time decision-making, predictive maintenance, and autonomous operations. However, this transformative power introduces a new paradigm of security challenges that traditional IT/OT tools are ill-equipped to handle.
This guide delves into the essential aspects of private network security, emphasizing that security isn’t merely an add-on feature, but an architectural imperative. We’ll explore where new threat surfaces emerge, clarify why private 5G security diverges significantly from Wi-Fi security, define what “secure-by-design” truly means in this context, and highlight the most common mistakes enterprises make as they transition from pilot projects to full-scale production.
The Evolving Landscape of Private Networks
Private wireless networks, encompassing private 5G, LTE, and CBRS, represent a fundamental shift in how enterprises manage their connectivity. Unlike public cellular networks operated by telecommunications providers, private networks give enterprises direct ownership and control over their wireless infrastructure. This autonomy offers unprecedented customization, reliability, and performance tailored to specific operational needs.
What is a Private 5G Network?
A private 5G network is a local cellular network, including its own base stations and 5G Core, designed for the exclusive use of an organization. It provides dedicated coverage and capacity, ensuring low latency, high bandwidth, and massive connectivity for a defined geographical area. This self-contained environment makes it ideal for mission-critical applications that require guaranteed performance and stringent security.
Why the Rapid Adoption?
Industries are increasingly turning to private 5G for several compelling reasons:
- Enhanced Performance: Superior speed, ultra-low latency, and greater capacity compared to Wi-Fi, crucial for real-time applications like autonomous vehicles and augmented reality.
- Reliability: Dedicated spectrum and infrastructure provide deterministic performance, minimizing interference and ensuring consistent service availability.
- Security: Greater control over network access and data handling within a private domain.
- Mobility: Seamless roaming and handover for devices across large operational areas, without performance degradation.
- Customization: Networks can be tailored to specific enterprise requirements, supporting specialized protocols and device types.
The rise of these networks, while bringing immense operational value, also introduces a complex and expanded threat surface that demands a specialized security approach.
Demystifying the New Threat Surfaces
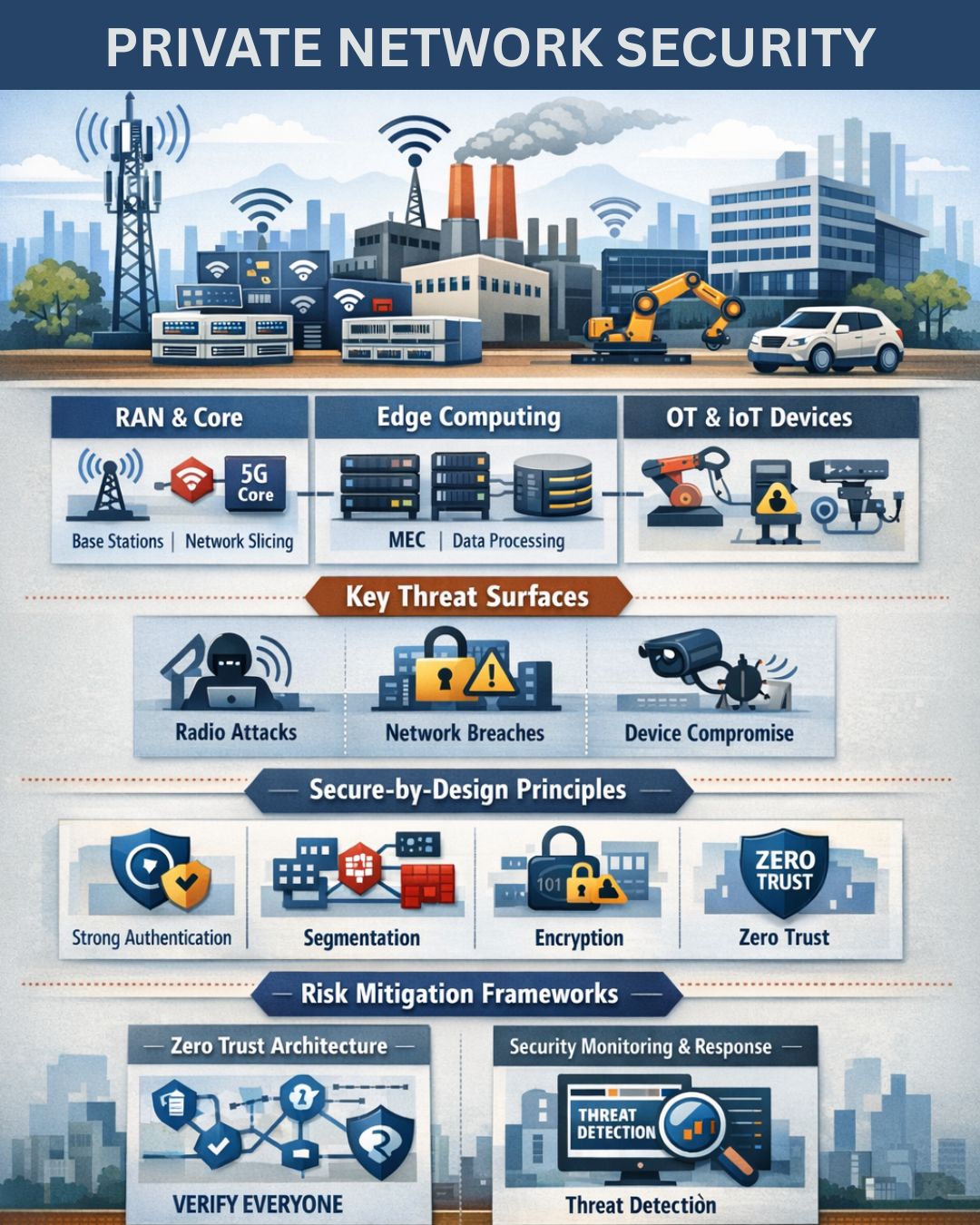
The convergence of IT, Operational Technology (OT), Internet of Things (IoT), and traditional cellular infrastructure within private 5G environments dramatically broadens the attack surface. Traditional security tools designed for Wi-Fi or wired networks are often inadequate for protecting this intricate ecosystem. Securing a modern private cellular network requires understanding the specific vulnerabilities inherent in its core components.
RAN & Core: The Foundation’s Vulnerabilities
The Radio Access Network (RAN) and 5G Core form the very heart of a private 5G network. Securing these components is paramount, as a compromise here can have catastrophic consequences.
- Base Stations (gNBs): These are the physical points of connection for devices to the network. Vulnerabilities can include physical tampering, unauthenticated access, or software exploits that allow attackers to eavesdrop on communications, inject malicious data, or disrupt network services. Radio frequency-level attacks can also target these elements.
- Network Slicing: A key feature of 5G, network slicing allows for the creation of multiple virtual networks on a shared physical infrastructure, each tailored for different service requirements. While offering flexibility, improper isolation between slices can lead to lateral movement for attackers or unauthorized access to sensitive data and services in other slices.
- 5G Core: The brain of the network, the 5G Core handles authentication, mobility management, session management, and other crucial functions. Security flaws in the Core’s control plane or user plane functions (e.g., AMF, SMF, UPF) could lead to denial-of-service attacks, subscriber information disclosure, or manipulation of network traffic. Threats include malware, insider threats, and sophisticated application-layer attacks.
Edge Computing: Processing Power at the Periphery
Edge computing brings data processing closer to the source, reducing latency and enabling real-time analytics for applications like autonomous systems and industrial IoT. However, distributing computing resources also distributes security risks.
- Multi-access Edge Compute (MEC): MEC platforms host applications at the edge of the network, often on premises. These environments introduce new vectors for attack, including vulnerabilities in the MEC platform itself, insecure applications deployed on it, or compromised containers/virtual machines.
- Data Processing at the Edge: As sensitive data is processed and stored locally at the edge, ensuring its confidentiality, integrity, and availability becomes critical. This includes data in transit and at rest on edge servers, which might reside in less physically secure environments than centralized data centers.
OT & IoT Devices: The Endpoint Explosion
The sheer volume and diversity of Operational Technology (OT) and Internet of Things (IoT) devices connecting to private 5G networks represent one of the most significant expansions of the threat surface. These devices often have limited security capabilities, long lifecycles, and may run outdated software.
- Connected Machinery and Autonomous Assets: Industrial robots, automated guided vehicles (AGVs), and other critical machinery become direct targets. A successful attack could lead to production shutdowns, physical damage, or safety hazards.
- Thousands of IoT/IIoT Sensors: From environmental sensors to smart meters, these devices collect vast amounts of data. Compromise can lead to data manipulation, espionage, or using the devices as entry points into the broader network.
- Legacy OT Systems via Gateways: Older OT systems were not designed with modern cybersecurity in mind. Bridging them to a private 5G network via gateways requires careful security considerations to prevent vulnerabilities from a legacy system from spreading into the 5G domain.
- Smart Factories and Campuses: The interconnected nature of these environments means a compromise in one area can quickly propagate, affecting numerous devices and systems.
Key Threat Surfaces in Summary
The image highlights three overarching categories of threats:
- Radio Attacks: Exploiting vulnerabilities in the wireless transmission itself, such as jamming, eavesdropping, or spoofing radio signals to disrupt communications or inject false data. These attacks target the RAN layer.
- Network Breaches: Unauthorized access to network infrastructure (Core, MEC, backhaul) through exploiting software vulnerabilities, weak authentication, or misconfigurations, leading to data exfiltration, service disruption, or control plane manipulation.
- Device Compromise: Gaining control over connected devices (OT, IoT, user equipment) through malware, exploiting software flaws, or physical tampering. Compromised devices can be used to launch further attacks, manipulate data, or cause physical damage.
Understanding these multifaceted threat surfaces is the first step towards building a resilient and secure private 5G network. As enterprises gain direct ownership of their wireless infrastructure, the security landscape dramatically expands, demanding visibility, identity assurance, and robust threat detection across all layers.
Why Private 5G Security is Not Wi-Fi Security
A common and critical misconception is to apply Wi-Fi security paradigms directly to private 5G networks. While both provide wireless connectivity, their underlying architectures, security mechanisms, and threat models are fundamentally different. Treating them similarly is a recipe for security vulnerabilities.
Architectural Differences Drive Security Disparities
- Identity and Authentication:
- Wi-Fi: Often relies on pre-shared keys (PSK), MAC address filtering, or 802.1X using RADIUS servers. Device authentication can be less robust and centralized.
- Private 5G: Built on cellular security standards that include strong, hardware-based authentication using Subscriber Identity Modules (SIMs) or eSIMs. The 5G Core performs mutual authentication (network authenticates device, and device authenticates network), providing a far more secure and tamper-resistant identity plane. Every device has a unique, cryptographically secured identity.
- Network Segmentation and Isolation:
- Wi-Fi: Basic VLANs provide some segmentation, but often lack granular control and can be susceptible to misconfiguration or bypass if not managed meticulously.
- Private 5G: Inherently designed with robust segmentation capabilities through core network functions and network slicing. This enables the creation of highly isolated logical networks with distinct policies and resources, providing a stronger defense in depth.
- Encryption and Integrity:
- Wi-Fi: Typically relies on WPA2/WPA3 for over-the-air encryption. While effective, vulnerabilities can arise from weak passphrase management or implementation flaws.
- Private 5G: Employs advanced, mandatory encryption and integrity protection from the device to the 5G Core, including strong cryptographic algorithms and sophisticated key management protocols. This ensures higher levels of data confidentiality and protection against tampering.
- Scale and Operational Continuity:
- Wi-Fi: While scalable, large-scale industrial Wi-Fi deployments can face issues with interference, handovers, and managing thousands of devices requiring ultra-low latency.
- Private 5G: Designed for massive scale, high connection density, and mission-critical applications. Security must therefore account for the impact of even minor disruptions on operational continuity, particularly in OT environments where downtime can be extremely costly or dangerous.
- Threat Model:
- Wi-Fi: Primarily focuses on protecting internal IT systems from external threats and unauthorized access to data.
- Private 5G: Extends the threat model to include not just IT and data, but also OT critical infrastructure, physical processes, and the availability of real-time services. The impact of a successful attack can extend from data breaches to physical sabotage or safety incidents.
The Dangers of Assumption
Assuming “private 5G is just like Wi-Fi, but faster” leads to:
- Underestimation of Risk: Enterprises fail to recognize the new and unique attack vectors introduced by cellular technologies, especially at the RAN and Core layers.
- Insufficient Investment: Budgeting for security based on Wi-Fi models dramatically undershoots the necessary investment in specialized expertise, tools, and processes required for private 5G.
- Inadequate Skillsets: Relying on IT teams with solely Wi-Fi experience to secure a private 5G network can leave critical vulnerabilities unaddressed. A blend of IT, OT, and cellular expertise is essential.
- Misguided Deployments: Implementing security controls that are robust for Wi-Fi but permeable for private 5G, leaving crucial gaps in the defense posture.
The distinctions are not merely technical minutiae; they are fundamental differences that necessitate a distinct and comprehensive security strategy. Private 5G, LTE, and CBRS bring robust native security features, but their secure deployment and operation still rely heavily on the enterprise’s architectural choices and ongoing security management.
Architecting Security from the Ground Up: Secure-by-Design Principles
In the context of private 5G, “secure-by-design” means embedding security considerations into every phase of network planning, deployment, and operation, rather than patching them on retrospectively. It’s about proactive risk mitigation, ensuring the foundational elements of the network are inherently resilient against threats.
Strong Authentication: Verifying Every Entity
At the core of secure-by-design is robust identity management for every entity connected to or operating within the private network. This moves beyond simple passwords or generic keys.
- Mutual Authentication: Ensuring both the device and the network cryptographically verify each other’s identity before establishing a connection. This prevents rogue devices from joining the network and protects legitimate devices from connecting to malicious networks.
- Hardware-Based Identity: Leveraging features like SIM/eSIM for device identity provides a strong, tamper-resistant root of trust.
- Centralized Identity Management: Integrating private 5G device identities with enterprise identity management systems (e.g., Active Directory) for consistent access policies.
- Multi-Factor Authentication (MFA): Where applicable for human users accessing network management interfaces, requiring multiple forms of verification.
Strong authentication forms the bedrock for trust, ensuring that only authorized users and devices can access network resources.
Segmentation: Dividing to Conquer Threats
Network segmentation is the practice of dividing a network into smaller, isolated logical segments. This limits the blast radius of a cyberattack, preventing an intruder from moving freely across the entire network if one segment is compromised.
- Micro-segmentation: Going beyond traditional VLANs, micro-segmentation applies granular security policies to individual workloads, applications, or devices. In a private 5G context, this could mean isolating specific OT devices, critical machines, or application servers.
- Network Slicing for Isolation: Leveraging 5G’s native network slicing capabilities to create distinct, logically isolated networks for different applications with varying security requirements (e.g., one slice for critical control systems, another for non-critical IoT sensors, and another for enterprise IT traffic).
- Policy-Based Segmentation: Dynamically enforcing access rules based on device identity, user role, application needs, and contextual factors.
- Separation of IT/OT/Cellular: Maintaining strict boundaries between traditional IT networks, operational technology networks, and the private cellular infrastructure to prevent IT vulnerabilities from impacting OT systems and vice-versa.
Effective segmentation acts as a firewall within the network, containing threats and making it significantly harder for attackers to achieve their objectives.
Encryption: Protecting Data in Transit and at Rest
Encryption is the process of scrambling data to prevent unauthorized access. In private 5G, it’s crucial for protecting sensitive information as it traverses the network and when it’s stored.
- End-to-End Encryption: Ensuring data is encrypted from the source device to the destination application, wherever possible, beyond just the over-the-air link.
- Over-the-Air Encryption: As provided by 5G standards, strong cryptographic protection for all radio communications between devices and base stations.
- Data at Rest Encryption: Encrypting sensitive data stored on edge computing servers, device storage, and core network components.
- Key Management: Implementing robust key management systems to securely generate, distribute, store, rotate, and revoke cryptographic keys.
Encryption provides confidentiality, safeguarding data from eavesdropping and unauthorized disclosure, a critical component for data integrity and privacy.
Zero Trust: Never Trust, Always Verify
Zero Trust is a security paradigm rooted in the principle that no user, device, or application, whether inside or outside the network perimeter, should be implicitly trusted. Every access request is continuously verified.
- Verify Explicitly: All access decisions are based on the totality of available information, including user identity, device identity, location, service being accessed, and real-time risk posture.
- Least Privilege Access: Granting only the minimum necessary permissions to users and devices for the shortest possible duration.
- Continuous Verification: Security posture is continuously monitored, and access can be revoked dynamically if conditions change or anomalous behavior is detected.
- Assume Breach: Designing security with the assumption that breaches will occur, and focusing on minimizing damage and rapid recovery.
Implementing Zero Trust principles across the converged IT, OT, IoT, and cellular domains is a cornerstone of modern private 5G security. It provides a unified security framework that enhances resilience, compliance, and long-term competitiveness.
Risk Mitigation Frameworks: Proactive Defense and Responsive Action
Even with secure-by-design principles in place, the dynamic nature of cyber threats necessitates robust risk mitigation frameworks. These frameworks focus on continuous monitoring, rapid response, and architectural resilience.
Zero Trust Architecture: Verifying Everyone, Everything, Always
The pictorial representation of Zero Trust Architecture emphasizes “VERIFY EVERYONE.” This concept extends beyond just human users to encompass every device, application, and workload attempting to access resources on the network.
- Unified Policy Management: Consolidating security policies for both private 5G and existing Wi-Fi/IT environments under a single Zero Trust framework ensures consistent enforcement.
- Micro-segmentation in Practice: Dynamic policies and micro-segmentation are key to enforcing least privilege access and continuously verifying the security posture of endpoints and workloads.
- Identity-Centric Security: All access control decisions revolve around the verified identity of the requesting entity (user, device, application), not just its network location.
- Contextual Access Decisions: Access is granted based on attributes like identity, device health, location, time of day, and the sensitivity of the data being accessed.
A well-implemented Zero Trust Architecture minimizes implicit trust, reduces the attack surface, and significantly enhances an organization’s ability to detect and respond to security incidents.
Security Monitoring & Response: Vigilance and Reaction
Effective security is not just about preventing attacks, but also about quickly detecting and responding to them when they occur. This requires continuous vigilance and a well-defined incident response plan.
- Threat Detection: Implementing advanced tools and techniques to identify malicious activities, anomalies, and potential security breaches in real-time.
- AI & Edge Intelligence: Leveraging Multi-Access Edge Computing (MEC) and Artificial Intelligence (AI) for real-time monitoring and local decision-making. AI/ML-driven analytics can identify subtle patterns indicative of a compromise that might be missed by human analysts.
- Behavioral Analytics: Monitoring the behavior of users, devices, and applications to detect deviations from established baselines.
- Vulnerability Management: Continuously scanning for and patching known vulnerabilities in network components, firmware, and applications.
- Security Information and Event Management (SIEM): Centralizing logs and security events from all private 5G components (RAN, Core, MEC, devices, firewalls) into a SIEM system for correlation, analysis, and comprehensive visibility.
- Incident Response Plan: Developing and regularly testing a clear, actionable plan for responding to security incidents, including containment, eradication, recovery, and post-incident analysis.
- Continuous Threat Intelligence: Staying updated on the latest threats, vulnerabilities, and attack techniques relevant to private cellular networks and the interconnected IT/OT/IoT environment.
By integrating robust security monitoring with a proactive response capability, enterprises can minimize the impact of security incidents and maintain operational continuity. The goal is not just to detect threats, but to have the intelligence and automation to respond effectively and efficiently.
Common Mistakes Enterprises Make
Deploying a private 5G network is a complex undertaking, and security can often be an afterthought or mishandled due. Avoiding common pitfalls is crucial for success.
1. Underestimating the Unique Security Challenges
Many enterprises fall into the trap of assuming that their existing IT security team and tools are sufficient for a private 5G network. This overlooks critical differences:
- Cellular Specifics: Lack of expertise in 3GPP standards, cellular protocol vulnerabilities, and the specialized security mechanisms of 5G (e.g., authentication key agreement, ciphering).
- OT Integration: Underestimating the unique security requirements and vulnerabilities of OT environments and the potential for a cellular network compromise to lead to physical world impacts.
- Converged Threat Landscape: Failing to recognize the complex interplay of IT, OT, IoT, and cellular threats, and the need for unified security policies.
2. Neglecting a Secure-by-Design Approach
Trying to bolt security onto a private 5G network after it’s been deployed is inherently less effective and more costly than designing it securely from the outset.
- Late Security Involvement: Security teams are brought in too late in the planning process, making it difficult to embed foundational security controls without significant re-architecture.
- Focus on Functionality Over Security: Prioritizing rapid deployment and operational features above comprehensive security measures, leading to shortcuts and vulnerabilities.
- Lack of Security Requirements in RFPs: Not clearly articulating specific security requirements for private 5G vendors and solutions during procurement.
3. Inadequate Identity and Access Management
Weak or poorly implemented identity and access controls remain a leading cause of breaches.
- Default Credentials: Failing to change default passwords or using weak credentials for devices, network elements, and management interfaces.
- Lack of Strong Device Authentication: Not fully leveraging SIM-based authentication or relying on less secure methods for IoT devices.
- Insufficient Role-Based Access Control (RBAC): Granting overly broad permissions to users or devices, violating the principle of least privilege.
- No Centralized Identity: Managing identities in silos across IT, OT, and cellular components, leading to inconsistencies and security gaps.
4. Poor Segmentation and Network Isolation
Failing to properly segment the private 5G network can allow an attacker to move laterally across the network and access critical assets.
- Flat Network Architectures: Deploying a flat network where all devices and applications reside on the same logical segment, offering minimal containment in a breach.
- Misconfigured Network Slices: Improperly configuring logical isolation between network slices, leading to potential cross-slice contamination.
- Blending IT/OT Without Controls: Directly connecting OT and IT networks through the private 5G network without strong mediating firewalls, intrusion detection/prevention systems (IDPS), and access controls.
5. Insufficient Visibility and Monitoring
You can’t secure what you can’t see. A lack of comprehensive visibility into network activity leaves organizations blind to ongoing threats.
- Lack of Centralized Logging: Not aggregating logs from all private 5G components and connected devices into a central SIEM.
- No Anomaly Detection: Relying solely on signature-based detection without behavioral analytics to spot unusual activity.
- Blind Spots: Not monitoring the RAN layer, traffic within network slices, or communications to/from edge computing instances.
- Limited Incident Response Planning: Having an underdeveloped or untested incident response plan, leading to panic and disorganized reactions during a breach.
6. Neglecting Endpoint Security for IoT/OT
The vast number of IoT and OT devices connected to private 5G makes them a prime target.
- Unpatched Devices: Failing to regularly patch and update firmware on IoT/OT devices, leaving known vulnerabilities exposed.
- Insecure Device Configurations: Deploying devices with default or weak security configurations.
- Lack of Device Baseline: Not establishing a baseline for normal device behavior, making it difficult to detect compromised devices.
- Limited Device Lifecycle Management: Not having processes for securely onboarding, managing, and decommissioning IoT/OT devices.
Avoiding these common mistakes requires a comprehensive and proactive security strategy, a skilled team, and appropriate tools tailored to the unique demands of private 5G networks.
Conclusion: Building a Secure Foundation for Innovation
Private 5G networks are not a futuristic pipe dream; they are a present-day reality, fueling unprecedented levels of automation, efficiency, and connectivity across industries. However, the true value of these networks can only be realized if they are built upon a foundation of unyielding security. Ignoring the distinct threat landscape and failing to adopt a secure-by-design approach transforms this powerful asset into a significant operational liability.
The journey from proof-of-concept to production for private 5G is complex. It demands a holistic understanding of the new threat surfaces emerging across the RAN, Core, Edge, Devices, and Management layers. It requires recognizing that private 5G security is fundamentally different from Wi-Fi security. Most importantly, it necessitates an architectural commitment to principles like strong authentication, robust segmentation, pervasive encryption, and a Zero Trust model that verifies every interaction.
By avoiding common pitfalls and investing in proactive defense and agile response mechanisms, enterprises can confidently leverage private 5G to unlock new possibilities, enhance competitiveness, and drive the next wave of industrial transformation—without compromising their critical operations or data. Security is not an impediment to innovation; it is its most essential enabler.
Unlock Your Private 5G Potential with IoT Worlds
Are you planning or currently deploying a private 5G network and concerned about ensuring its robust security? Do you need expert guidance to navigate the complex landscape of cellular, IT, and OT converged security?
At IoT Worlds, we specialize in empowering businesses to harness the full power of private networks while mitigating risks. Our team of seasoned consultants brings deep expertise in private 5G architecture, cybersecurity strategy, Zero Trust implementation, and comprehensive risk management. We can help you:
- Assess your current security posture and identify vulnerabilities.
- Design a secure-by-design private 5G architecture tailored to your unique operational needs.
- Implement robust authentication, segmentation, and encryption strategies.
- Develop and integrate a comprehensive Zero Trust framework.
- Establish effective security monitoring and incident response capabilities.
- Train your teams to manage and maintain a secure private network.
Don’t let security concerns hinder your private 5G journey. Partner with IoT Worlds to build a resilient, high-performing, and secure network that truly drives your business forward.
Ready to secure your private 5G network from pilot to production?
Send an email to info@iotworlds.com to schedule a consultation and take the first step towards building cutting-edge, secure private network solutions for your enterprise.