Industrial organizations don’t lose sleep over “cyber maturity scores.” They lose sleep over unplanned downtime, safety risk, product quality issues, regulatory exposure, and the fear that a single compromised remote connection could cascade from IT into OT—right when the plant is running at full capacity.
That’s exactly why NIST Cybersecurity Framework 2.0 (CSF 2.0) has become such a useful organizing model. It gives executives, plant leaders, engineers, IT, and security teams a shared language of outcomes: what you’re trying to achieve, how you prioritize it, and how you measure progress.
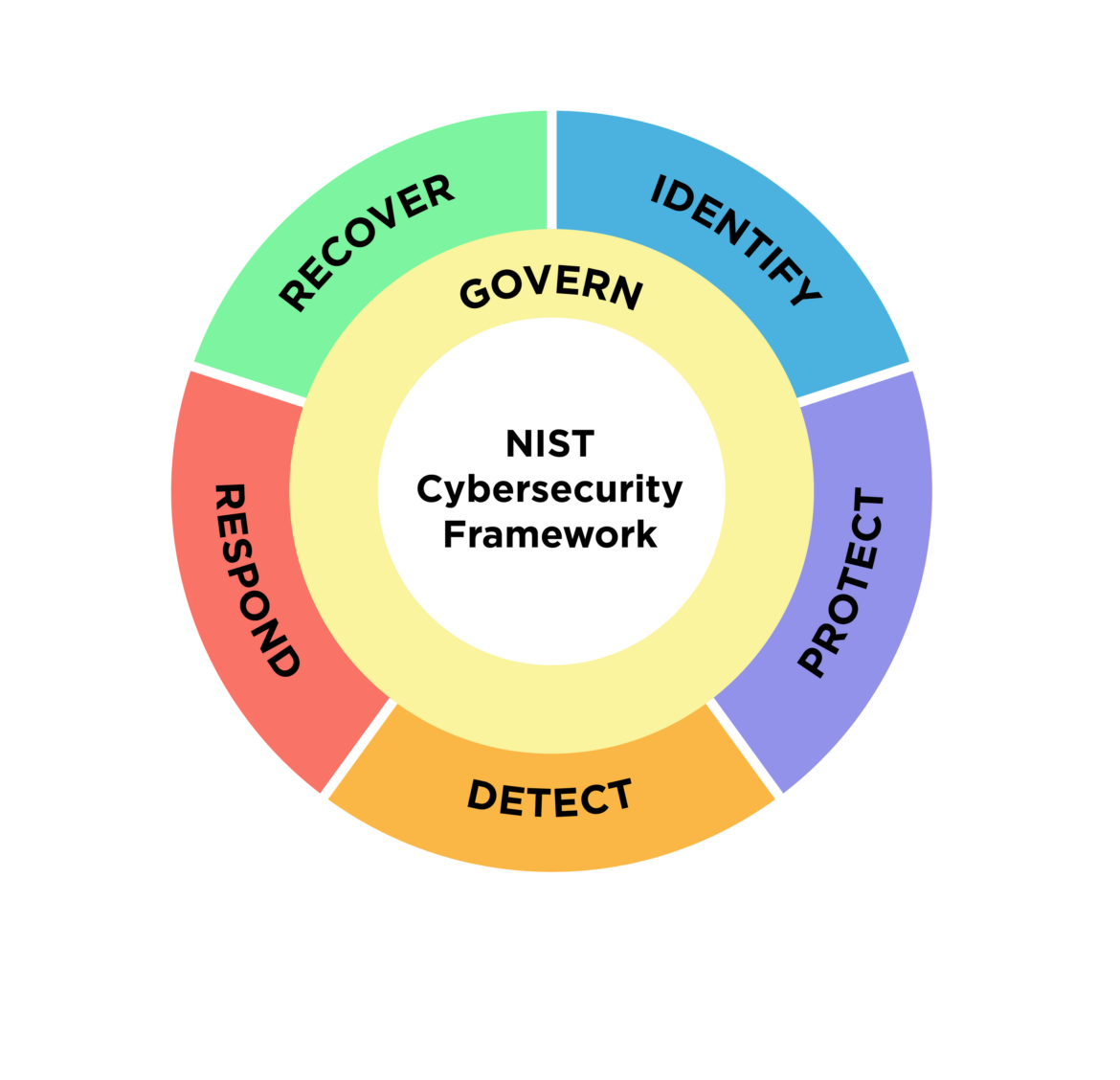
CSF 2.0 is also a major update. NIST released CSF 2.0 on 2024 and explicitly added a new top-level function: GOVERN—bringing the total to six functions: Govern, Identify, Protect, Detect, Respond, Recover.
For OT and Industrial IoT (IIoT), that’s not a minor change. It’s an upgrade that finally reflects the reality of industrial security:
- You can’t always patch immediately.
- You can’t always scan actively.
- You can’t always reboot safely.
- You must know who owns the risk decisions—and how those decisions get made.
This guide is written for iotworlds.com readers and focuses on practical CSF 2.0 implementation in OT/IIoT: remote access, segmentation, passive monitoring, vendor governance, incident response that respects safety, and recovery that actually restores production.
What is CSF 2.0?
CSF 2.0 is NIST’s risk-based cybersecurity framework that helps organizations understand, assess, prioritize, and communicate cybersecurity risk using a common structure of outcomes.
What’s new in CSF 2.0?
CSF 2.0 introduces a new function—GOVERN—and adds stronger emphasis on governance and supply chain considerations.
Why does CSF 2.0 matter for OT and IIoT?
OT and IIoT environments are constrained by safety, uptime, legacy protocols, and vendor dependencies. CSF 2.0 helps you build a program that is risk-driven, measurable, and operationally realistic, with clear decision-making and accountability under GOVERN.
1) CSF 2.0 For Industrial Leaders
CSF 2.0 is a framework for answering four questions in a way everyone can agree on:
- What are we responsible for protecting (and why)?
- What outcomes should our cybersecurity program achieve?
- Where are we today vs. where do we need to be?
- How do we prioritize investments to reduce risk without disrupting operations?
It’s not a product, not a tool, and not a compliance checklist. It’s a program blueprint—and in OT/IIoT, that’s often the missing piece.
2) What Changed in CSF 2.0 (And Why “GOVERN” Changes Everything)
NIST’s own release messaging highlights that CSF 2.0 expands beyond critical infrastructure origins and adds new emphasis on governance, along with implementation resources to support organizations.
The headline change: GOVERN becomes a top-level function
CSF 2.0 organizes the Framework Core around six functions:
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
Why this matters specifically in OT/IIoT
In industrial environments, cybersecurity often fails at the seams:
- IT owns “security,” but OT owns the systems.
- Engineering owns changes, but security owns risk.
- Vendors need access, but procurement owns contracts.
- Operations prioritizes uptime, but incident response needs containment.
GOVERN forces the organization to define:
- decision rights,
- accountability,
- risk appetite,
- policy constraints,
- third-party governance,
- and performance oversight.
Without that, Identify/Protect/Detect/Respond/Recover becomes a collection of disconnected initiatives.
3) CSF Core Components: Core, Profiles, and Implementation Tiers (OT/IIoT Lens)
Here’s how industrial teams should interpret them.
3.1 Framework Core: outcomes, not a checklist
The Core is the “what”: a structured set of cybersecurity outcomes organized by function.
OT translation: the Core is a shared map for aligning safety, reliability, uptime, and security into one improvement plan.
3.2 Profiles: your Current vs. Target state (most important for factories)
Profiles turn CSF from concept into roadmap:
- Current Profile: what you can truthfully claim today
- Target Profile: the outcomes you need based on risk
- Gap: the work you prioritize, fund, and execute
Industrial reality: you may accept that certain PLCs cannot be patched quarterly. Your Target Profile should reflect compensating controls (segmentation, remote access hardening, monitoring, backups, recovery drills) rather than unrealistic patch mandates.
3.3 Implementation Tiers: maturity as consistency
Tiers describe the maturity of your risk management practices (from ad hoc to adaptive).
OT twist: many organizations are “Tier 2 overall” but “Tier 3” in change control (because operations already requires discipline), and “Tier 1” in asset inventory (because nobody wants to disrupt the plant). CSF supports uneven maturity—your job is to improve the riskiest gaps first.
4) CSF 2.0 Functions for OT + IIoT (One Table to Align the Organization)
| CSF 2.0 Function | OT/IIoT Meaning | Typical Evidence | Common Failure Mode |
|---|---|---|---|
| GOVERN | Define ownership, risk appetite, policies, third-party rules, reporting | OT cyber charter, RACI, vendor access policy, risk acceptance workflow | “Security is IT’s job” (no plant accountability) |
| IDENTIFY | Know assets, dependencies, criticality, risk scenarios | OT asset inventory, network diagrams, data flows, criticality ranking | Inventory stops at IP layer (misses field devices, backplane/serial, shadow IIoT) |
| PROTECT | Reduce likelihood/impact through safeguards | segmentation, remote access controls, hardening, backups, training | patch-only strategy in a compensating-control world |
| DETECT | Find abnormal behavior early | passive monitoring, baselines, alert triage process | noisy alerts with no owner or response path |
| RESPOND | Contain/eradicate with safety + uptime constraints | OT incident playbooks, isolation procedures, vendor escalation | copying IT playbooks into OT (unsafe steps) |
| RECOVER | Restore operations and improve resilience | tested restores, golden images, DR runbooks, lessons learned | backups exist but restores fail, are incomplete, or are untested |
5) GOVERN: The Industrial Cybersecurity Multiplier
If you want the fastest CSF 2.0 win in OT/IIoT, start here.
5.1 Define decision rights with an OT Cyber RACI
A simple “who decides” matrix prevents 80% of execution failure.
Minimum roles to include:
- Plant manager / operations leader
- OT/controls engineering manager
- IT security / SOC lead
- Network engineering
- Safety and compliance
- Reliability/maintenance
- Procurement/vendor management
- Key integrators/OEMs (where appropriate)
Decisions you must assign:
- Approving downtime for remediation
- Approving isolation of a cell/line
- Approving vendor remote access
- Accepting risk when patching isn’t possible
- Approving monitoring methods (passive vs active)
- Declaring an OT incident and escalation triggers
5.2 Establish risk appetite and an OT risk acceptance process (not a loophole)
Risk acceptance in OT should include:
- risk statement tied to safety/availability impact
- compensating controls
- expiration date + review cadence
- accountable approver (often plant leadership)
- linkage to evidence (inventory, monitoring, segmentation)
This becomes your “governance backbone” for vulnerability management, exceptions, and operational constraints.
5.3 Govern vendor access like it’s part of your perimeter (because it is)
Industrial attackers love vendor pathways: shared accounts, always-on VPNs, unmanaged laptops, unclear authentication, and weak session oversight.
Baseline outcomes to target:
- unique vendor identities (no shared logins)
- MFA for remote access into OT
- least privilege and time-bounded approvals
- recorded sessions for critical systems
- clear contract language: notification, security requirements, and support for secure access
5.4 Create governance-grade reporting
Leadership needs metrics that translate to risk:
- % of critical remote access sessions using MFA and approvals
- number of flat-network segments eliminated
- recovery time for critical systems (measured via drills)
- detection coverage of critical zones
- time-to-triage for high severity OT alerts
6) IDENTIFY in OT/IIoT: Visibility Without Disruption
“Asset inventory” in OT is not a spreadsheet. It’s process awareness.
6.1 What “complete” inventory means for industrial environments
Include, at minimum:
- PLCs, RTUs, relays, drives, HMIs, historians
- engineering workstations and jump hosts
- managed switches, firewalls, wireless links
- safety systems (with special governance and access rules)
- IIoT sensors, gateways, edge compute nodes
- cloud services collecting plant telemetry (dashboards, predictive maintenance platforms)
- dependencies: DNS/NTP/domain services/backup repositories
6.2 Identify criticality: process-aware ranking
Rank by:
- Safety impact (injury/environment risk)
- Availability impact (downtime cost, throughput loss)
- Quality impact (scrap/rework/regulatory recall)
- Recoverability (lead time for replacement, vendor availability)
- Connectivity risk (internet-facing paths, vendor tunnels, IT/OT conduits)
6.3 Identify trust boundaries and data flows (the IIoT reality)
IIoT introduces new paths:
- edge gateways to cloud
- cellular-connected devices
- remote dashboards and APIs
- vendor-managed platforms
- “temporary” remote access that becomes permanent
Your Identify function should document these as systems and dependencies, not as “miscellaneous IT stuff.”
7) PROTECT: Industrial Controls That Reduce Risk Without Breaking Production
OT security succeeds when it respects constraints and still reduces risk.
7.1 Segmentation: the control that pays back repeatedly
Segmentation reduces blast radius and simplifies monitoring.
Common segmentation layers:
- IT / OT separation with a controlled DMZ
- zones per line/cell/skid
- conduits with allowlists (east-west control)
- restricted pathways for historians and data egress
Practical tip: prioritize segmentation around your highest consequence processes and most connected assets first.
7.2 Remote access hardening: make it boring, auditable, and time-bounded
Minimum outcomes:
- MFA for all OT remote access
- jump-hosted access (avoid direct-to-asset whenever possible)
- unique accounts + least privilege
- session logging/recording for critical systems
- approvals tied to tickets/change windows
This is one of the highest ROI controls in industrial cybersecurity.
7.3 Configuration hardening and change control
OT teams already understand “change control.” Add security outcomes:
- golden builds for engineering workstations
- controlled software installation
- removable media controls
- backups of PLC logic, HMI projects, network configs
- audit trail of logic changes (where feasible)
7.4 Protect integrity first (often more important than confidentiality)
For many industrial systems, data confidentiality matters—but integrity and availability matter more:
- unauthorized logic changes are catastrophic
- tampered recipes can cause unsafe output
- historian integrity affects investigations and compliance
8) DETECT: Passive-First Monitoring for OT + IIoT (What Works in Real Plants)
Detection is where OT security becomes operational resilience—or becomes noise.
8.1 Passive monitoring (default choice for OT)
Passive monitoring collects visibility without generating extra traffic (e.g., SPAN/TAP).
Why industrial teams prefer passive:
- lowers risk of crashing fragile devices
- avoids adding traffic to deterministic networks
- reveals industrial protocols and command patterns
- supports baseline behavior modeling
Best early wins:
- new device detection
- new communications relationship detection
- unusual remote sessions
- unusual write commands (where protocol visibility permits)
8.2 Active monitoring: use surgically, with approvals
Active scanning can be valuable, but in OT it must be governed:
- schedule within maintenance windows
- validate with vendors and safety
- tune to low impact settings
- pilot on a small segment first
Your GOV-Detect connection: the ability to do any active assessment safely is largely a governance problem (approval paths, maintenance windows, and risk sign-off).
8.3 Reduce alert fatigue with process-aware detections
Prioritize detections tied to consequence:
- PLC programming session outside approved window
- new remote access session without an approved ticket
- new device in a safety zone
- unexpected writes to critical registers
- lateral movement attempts across zones
Define a triage model (example):
- Safety/availability threat
- Probable compromise
- Policy deviation / hygiene issue
9) RESPOND: OT Incident Response That Respects Safety and Uptime
The fastest way to fail in OT is to apply IT incident response playbooks verbatim.
9.1 Build OT-specific playbooks for top scenarios
At minimum:
- ransomware in enterprise with potential OT spread
- compromised engineering workstation
- suspected PLC logic change
- remote access compromise (vendor or contractor)
- malware on HMI/operator station
- network device compromise (switch/firewall)
- loss of historian / loss of visibility
Each playbook should include:
- safety checks and stop-work triggers
- escalation map (controls engineer, vendor, plant leadership)
- containment steps that preserve process stability
- evidence collection guidance that avoids disruption
9.2 Communications are a control
When an incident happens, the organization needs to know:
- who declares the incident
- who can approve isolation and downtime
- how to engage vendors and integrators
- what triggers regulatory/customer notification
CSF 2.0’s GOVERN function exists largely to prevent response chaos at the worst possible moment.
10) RECOVER: Recovery Is a Capability (Not a Backup Checkbox)
Many industrial teams “have backups” but discover during crisis that:
- PLC logic backups are outdated
- licensing servers are missing
- restore steps are undocumented
- safety validation after restore is unclear
- lead times for critical devices are months
10.1 The OT recovery stack (what must be recoverable)
Plan recovery for:
- PLC logic and configurations
- HMI/SCADA projects
- historian configs and critical data stores
- engineering workstation images (golden builds)
- network device configurations (switch/firewall/router)
- jump servers and remote access infrastructure
- documentation: diagrams, I/O lists, vendor contacts, restore runbooks
10.2 Test restores like you test safety systems
Recovery readiness should include:
- scheduled restore drills for critical systems
- measured restore time and success rate
- ransomware-resilient backup approach (offline/immutable where feasible)
- post-restore validation checklist (safety, quality, throughput)
Recovery is one of the most measurable cybersecurity outcomes in OT—and one leadership understands immediately.
11) Implementing CSF 2.0 in OT/IIoT: A Step-by-Step Roadmap
This is a practical “how to start and finish” path.
Phase 1 (Weeks 1–4): Build the foundation (GOVERN + Identify)
Deliverables:
- OT cybersecurity charter (scope + objectives)
- OT cyber RACI and decision rights
- risk acceptance process + exception workflow
- initial critical asset list (top 20% consequence systems)
- documented remote access pathways (vendor + internal)
Quick win: enforce MFA and unique identities for OT remote access wherever possible.
Phase 2 (Weeks 5–12): Define Profiles and prioritize (Profile-based program)
Workshops to run:
- Current Profile workshop (what is true today)
- Target Profile workshop (what outcomes you need next)
- gap analysis and prioritization (risk reduction vs effort)
Outcome: a roadmap leadership can fund and plants can execute.
Phase 3 (Months 3–6): Protect and Detect in the highest-risk zones
High ROI implementation themes:
- segmentation and DMZ improvements
- standard remote access pattern (jump host + MFA + approvals)
- passive monitoring for critical zones
- alert triage workflow with clear ownership
Phase 4 (Months 6–12): Respond and Recover maturity
Operational resilience deliverables:
- OT incident playbooks finalized + exercised
- tabletop exercises with realistic constraints
- restore runbooks and restore drills
- metrics and reporting cadence (board/leadership + plant ops)
12) CSF 2.0 Tiers in Industrial Reality (What “Good” Looks Like)
Use Tiers as a consistency lens:
- Tier 1 (Partial): ad hoc controls, limited visibility, inconsistent vendor access controls
- Tier 2 (Risk-Informed): policies exist; execution varies site-to-site
- Tier 3 (Repeatable): standards and practices consistent; monitoring and response are operationalized
- Tier 4 (Adaptive): continuous improvement, threat-informed tuning, strong governance and metrics
A mature OT organization often becomes Tier 3 in its critical zones first, then scales.
13) Mapping CSF 2.0 to Industrial Standards (Keep CSF as the “Program Layer”)
Most industrial orgs already use other guidance:
- IEC 62443 for zone/conduit design and system security requirements
- ISO/IEC 27001 for management system and audit structure
- NIST SP 800-53 for control catalog mapping (common in regulated environments)
CSF 2.0 is best used as your program-level framework—the structure that aligns stakeholders, defines outcomes, and measures progress—while other standards provide depth for specific control requirements.
NIST also provides supporting implementation resources and tools around CSF 2.0, including reference tooling and “informative references” to map to other documents.
14) OT/IIoT Metrics That Matter (Leadership-Grade KPIs)
Avoid “number of vulnerabilities” as your headline metric in OT. Prefer metrics that represent risk reduction and resilience:
Recommended CSF 2.0 OT KPIs
- Asset visibility coverage: % of critical assets inventoried and classified
- Remote access hygiene: % of OT remote sessions using MFA + approvals + unique identities
- Segmentation progress: number of flat segments reduced; number of enforced conduits
- Detection effectiveness: mean time to triage high-severity OT alerts; alert-to-action ratio
- Response readiness: number of OT playbooks tested; tabletop findings closed
- Recovery readiness: restore success rate; time-to-restore for critical systems (measured)
Tie these metrics directly to GOVERN reporting cadences so they become part of how the business manages operational risk.
15) Common CSF Mistakes in OT/IIoT (And How to Avoid Them)
Mistake 1: Treating CSF as a control checklist
Fix: Use Profiles to define outcomes and prioritize the roadmap.
Mistake 2: Forcing IT scanning/patching rhythms onto fragile OT environments
Fix: Use passive-first monitoring, maintenance windows, and compensating controls.
Mistake 3: Ignoring vendors as part of your security perimeter
Fix: Govern vendor access, contracts, identities, and session oversight under GOVERN.
Mistake 4: Measuring activity instead of resilience
Fix: Track restore success rates, remote access compliance, segmentation, and time-to-triage.
Mistake 5: “Backups exist” without restore drills
Fix: Treat recovery as a tested operational capability, not a storage problem.
16) FAQ (SEO + GEO Friendly)
What is the NIST Cybersecurity Framework 2.0 (CSF 2.0)?
CSF 2.0 is NIST’s updated cybersecurity framework that helps organizations understand, assess, prioritize, and communicate cybersecurity risk through a structured set of outcomes and implementation guidance.
What functions are in CSF 2.0?
CSF 2.0 includes six functions: Govern, Identify, Protect, Detect, Respond, and Recover.
What is the GOVERN function in CSF 2.0?
GOVERN is the function that focuses on cybersecurity governance: establishing objectives, direction, accountability, and oversight so cybersecurity aligns with enterprise risk management and mission outcomes.
Is CSF 2.0 suitable for OT and Industrial IoT?
Yes. CSF 2.0 is outcome-based and flexible, which makes it well-suited to OT/IIoT constraints like uptime requirements, legacy endpoints, vendor access, and safety-critical operations.
Should OT networks use passive or active monitoring?
Most OT environments should adopt passive monitoring first to reduce operational risk. Active scanning can be used selectively with governance controls (approvals, low-impact settings, and maintenance windows).
Conclusion: CSF 2.0 Is the OT/IIoT Operating Model—GOVERN Makes It Executable
CSF 2.0 works for industrial environments because it doesn’t demand a perfect world. It gives you a structured way to decide:
- what matters most,
- what you can realistically implement,
- what you must monitor continuously,
- how you will respond safely,
- and how you will recover production reliably.
The addition of GOVERN is the biggest practical upgrade for OT/IIoT teams because it makes accountability, decision rights, vendor access, and risk acceptance explicit—the exact areas where industrial cybersecurity programs most often stall.