Identity and Access Management (IAM) is a cornerstone of modern cybersecurity, ensuring that the right individuals have the appropriate access to the right resources at the right time. In the Information Technology (IT) world, IAM has matured into a sophisticated discipline, characterized by centralized systems, standardized protocols, and automated processes. However, when we shift our focus to Operational Technology (OT) environments, the landscape of IAM governance transforms dramatically. The seemingly straightforward principles of IT IAM often falter in the unique and demanding realm of OT.
This article delves into the fundamental differences between OT IAM and IT IAM governance, illuminating why a direct application of IT models to critical industrial systems is not only ineffective but also potentially dangerous. We will explore the inherent complexities of OT—from multi-vendor ecosystems and legacy infrastructure to stringent safety requirements and fragmented networks—and articulate why a specialized, risk-based, vendor-aware, and safety-first approach is paramount for securing industrial operations.
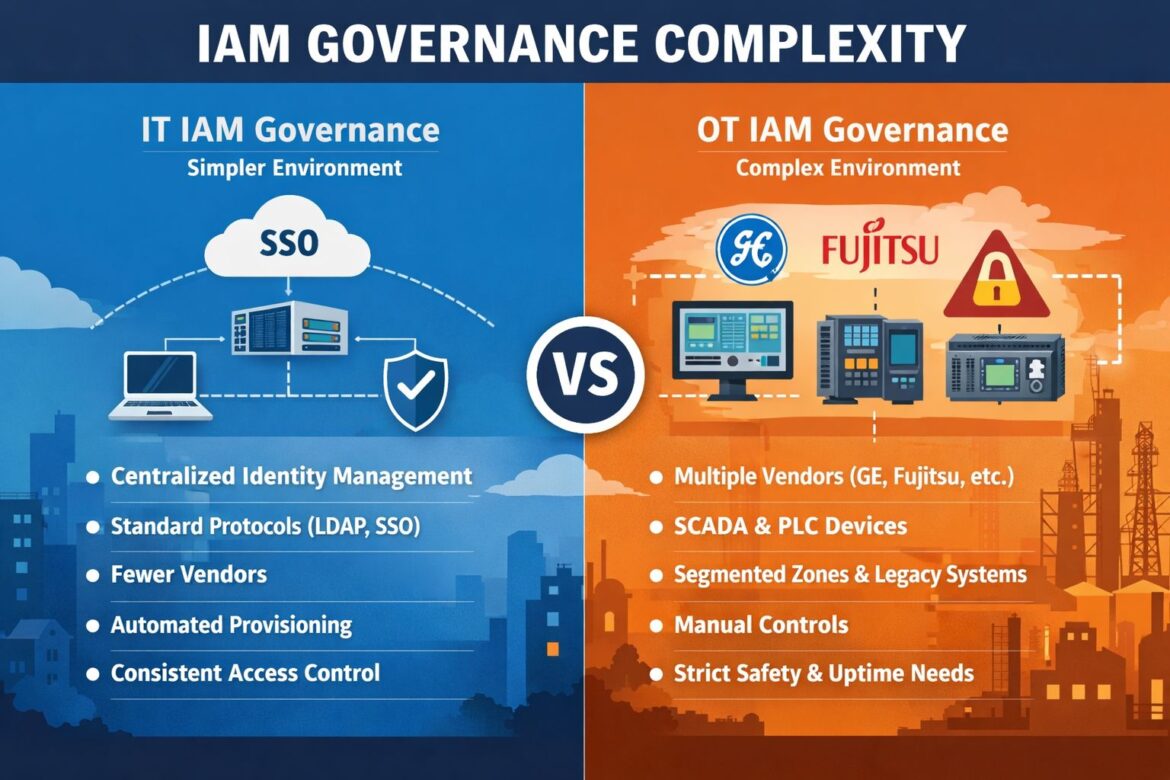
The Foundations of IT IAM Governance: A Simpler Environment
In the typical IT environment, IAM governance thrives on a set of well-established principles and technologies that create a relatively simpler and more streamlined security posture.
Centralized Identity Management
At the heart of IT IAM is the concept of centralized identity management. This means that user identities, their attributes, and their access privileges are managed from a single, authoritative source.
Benefits of Centralization in IT
Centralization in IT offers numerous advantages:
- Unified View: Administrators gain a holistic view of all users and their access rights across the entire IT infrastructure.
- Simplified Administration: User onboarding, offboarding, and changes to access permissions can be managed from one console, reducing administrative overhead.
- Enhanced Security: A centralized system allows for consistent application of security policies, easier auditing, and faster incident response by identifying and revoking compromised accounts quickly.
- Improved Compliance: Meeting regulatory requirements for access control and data protection becomes more manageable with a single source of truth for identity information.
Standard Protocols and Practices
IT environments largely rely on widely adopted standards and protocols for identity and access management. These standards facilitate interoperability and streamline integration across diverse applications and services.
Key IT IAM Protocols
- LDAP (Lightweight Directory Access Protocol): A mature and widely used protocol for accessing and maintaining distributed directory information services, often serving as the backbone for centralized identity stores like Microsoft Active Directory.
- SSO (Single Sign-On): A critical component of modern IT IAM, SSO allows users to authenticate once and gain access to multiple independent software systems without re-authenticating. This enhances user experience and reduces password fatigue, thereby improving security by minimizing the use of weak or reused passwords.
- Federated Identity Management: Protocols like SAML (Security Assertion Markup Language) and OAuth (Open Authorization) enable users to use a single set of credentials to access services across different organizations or identity providers, common in cloud environments.
Fewer Vendors and Streamlined Integration
While IT environments certainly feature a variety of software and hardware, the number of identity vendors tends to be more consolidated. This leads to better integration capabilities.
Advantages of Vendor Consolidation in IT
- API-Driven Integration: Modern IT systems are often built with APIs (Application Programming Interfaces) that allow for seamless integration with a centralized IAM solution.
- Reduced Complexity: A smaller number of primary vendors for identity infrastructure — e.g., Microsoft for Active Directory, Okta for SSO — simplifies management and troubleshooting.
- Consistent Policies: With fewer vendors, it’s easier to enforce consistent access control policies across the organization.
Automated Provisioning
Automation is a key differentiator in IT IAM governance. Capabilities for automated user provisioning and de-provisioning are standard.
How Automation Benefits IT
- Efficiency: Automating the creation, modification, and deletion of user accounts and access rights significantly reduces manual effort and human error.
- Timeliness: New employees gain access to necessary resources almost immediately upon joining, while departing employees have their access revoked promptly, minimizing security risks.
- Scalability: Automated provisioning allows IT systems to scale identity management operations efficiently as the organization grows.
Consistent Access Control
In IT, the goal is often to establish a consistent framework for access control that applies across various applications and data sources.
Principles of Consistent Access Control in IT
- Role-Based Access Control (RBAC): Users are assigned roles, and these roles are granted specific permissions. This simplifies management and ensures that users only have access relevant to their job function.
- Principle of Least Privilege (PoLP): Users are given the minimum level of access necessary to perform their duties, reducing the attack surface.
- Attribute-Based Access Control (ABAC): A more granular approach where access decisions are made based on attributes of the user, resource, and environment.
These foundational elements contribute to an IT IAM governance model that is relatively simpler to implement and maintain, offering a robust security posture for information assets.
The Complexities of OT IAM Governance: A Different Beast Entirely
In stark contrast to IT, Operational Technology environments introduce a multitude of complexities that transform IAM governance into a significantly more challenging endeavor. The core mission of OT—to ensure the continuous, safe, and reliable operation of physical processes—dictates a different set of priorities and constraints that often conflict with traditional IT security practices.
Multi-Vendor Complexity
OT environments are inherently multi-vendor, featuring a heterogeneous mix of hardware and software from numerous manufacturers. This is a fundamental characteristic that profoundly impacts IAM.
The Reality of Diverse OT Vendors
- Proprietary Access Models: Unlike the standardized protocols common in IT, many OT vendors, such as GE and Fujitsu, develop their own proprietary access models. These systems were often designed in an era before widespread connectivity and, as such, lack built-in support for modern IAM integration.
- Lack of Standardization: The absence of universal standards for identity and access management across different OT vendors means that each system may require a unique approach to managing users and privileges. This creates siloes and significantly increases the complexity of establishing a unified IAM strategy.
- Integration Challenges: Interoperability between disparate vendor systems for identity purposes is often limited or non-existent, making it difficult to achieve a single pane of glass for OT access management. This often necessitates manual workarounds or custom integrations, which are costly and difficult to maintain.
Heterogeneous Devices with Legacy Protocols
The operational heart of any industrial environment is a diverse array of devices, many of which are decades old and were never designed with modern cybersecurity or IAM in mind.
The Challenge of Legacy OT Infrastructure
- SCADA Systems, PLCs, RTUs: Supervisory Control and Data Acquisition (SCADA) systems, Programmable Logic Controllers (PLCs), and Remote Terminal Units (RTUs) are the workhorses of OT. These devices often run on operating systems that are no longer supported, with embedded firmware that cannot be easily updated.
- Limited Processing Power: Many legacy OT devices have limited processing power and memory, making them incapable of running modern authentication agents or encryption protocols.
- Outdated Communication Protocols: These systems often communicate using legacy, unencrypted protocols that are vulnerable to eavesdropping and manipulation. Integrating modern IAM with these protocols is a significant technical hurdle.
- Shared Accounts and Hardcoded Credentials: A common practice in older OT systems is the use of shared local accounts or even hardcoded credentials, which are anathema to modern IAM principles. The difficulty in eliminating these without disrupting operations poses a critical security risk.
- Lack of Authentication Support: Some legacy OT equipment simply doesn’t support active authentication at all, relying instead on physical security or network segmentation as their primary form of access control.
Highly Segmented Networks
OT networks are typically segmented into numerous small zones and conduits, a practice originally implemented for operational resilience and safety rather than cybersecurity. While beneficial for containing some threats, this segmentation adds significant complexity to IAM.
Implications of Network Segmentation for IAM
- Granular Access Governance: Managing access across these highly granular segments requires an equally granular approach to IAM. This means defining and enforcing precise access rules for every zone and every device within it.
- Harder to Manage: The sheer number of segments and the tight controls over network ports make it challenging to implement and manage a coherent IAM strategy that spans the entire OT environment.
- Network Connectivity Issues: Reliable network connectivity to a centralized identity provider, a staple of IT IAM, may not be available or guaranteed across all OT segments, particularly in remote or geographically dispersed industrial sites. This can disrupt authentication processes and impact operational continuity.
- Air-Gapped Systems: Some critical OT systems may be air-gapped, meaning they have no direct network connection to the outside world. While this offers strong protection, it also means traditional network-based IAM solutions are not applicable.
Safety and Availability First
The absolute priority in OT is the safety of personnel, the environment, and the continuous availability of critical operations. Any IAM implementation must never compromise these paramount considerations.
Operational Constraints on IAM Practices
- Limited MFA Adoption: While Multi-Factor Authentication (MFA) is a standard security practice in IT, its implementation in OT can be problematic. Authentication delays introduced by MFA prompts, even a few seconds, can interfere with real-time control operations or prevent immediate operator access during an emergency.
- Infrequent Credential Rotation: Regular password changes, a common IT best practice, can be difficult to implement for OT systems, especially those with shared accounts or embedded credentials, without risking operational disruption.
- Restricted Automated Provisioning: The cautious nature of OT environments often means that automated provisioning and de-provisioning, while efficient in IT, might be limited or require extensive manual oversight to prevent unintended consequences.
- Account Lockouts and Delays: In an IT system, an account lockout due to too many failed login attempts is a security measure. In OT, such a lockout could prevent emergency response personnel from accessing a critical safety system, leading to dangerous situations. Systems need to remain accessible during network outages or maintenance.
- Impact of Downtime: Any security measure that introduces the risk of downtime is viewed with extreme caution in OT. The cost of a few minutes of interrupted production can be enormous, let alone the potential safety implications.
Lower IAM Maturity than IT
Compared to the mature IAM landscape in IT, the development and adoption of robust IAM practices in OT environments have historically lagged. This results in a more fragmented and manual approach to identity and access.
Historical Context and Current State
- Fragmented IAM: While IT benefits from centralized IAM solutions, OT environments often have disparate and localized access control mechanisms for different systems and devices, leading to a fragmented and inconsistent security posture.
- Manual Processes: Many OT access management tasks, from user provisioning to privilege reviews, are still performed manually. This is time-consuming, prone to human error, and difficult to audit effectively.
- Limited SSO Adoption: Single Sign-On, a standard convenience and security enhancement in IT, is rare in OT due to the technical challenges of integrating with legacy systems and the operational concerns around potential points of failure.
- Focus on Physical Security: Historically, OT security relied heavily on physical barriers and isolated networks, rather than sophisticated digital identity management.
- Lack of Unified Security Strategy: For years, IT and OT had separate security strategies. This created silos and risks, as modern cyberattacks increasingly target OT. Manufacturers now realize the need for a single, unified security model covering both IT and OT.
- Conflicting Priorities: The traditional IT focus on data confidentiality often clashes with OT’s paramount focus on safety, reliability, and production continuity.
The convergence of IT and OT further highlights these challenges, demanding new strategies that can bridge the gap without compromising the unique operational requirements of industrial systems.
The Perils of Applying IT IAM Models Directly to OT
Given the inherent differences between IT and OT, a “lift and shift” approach, attempting to transplant IT IAM models directly into OT environments, is fraught with peril. Such an endeavor can lead to operational disruptions, increased security risks, and ultimately, a breakdown in critical industrial processes.
Operational Disruption and Downtime
The most immediate and concerning consequence of misapplying IT IAM to OT is the risk of operational disruption and costly downtime.
How IT IAM Can Halt Production
- Authentication Delays: Features like frequent MFA prompts or complex password policies, standard in IT, can introduce unacceptable delays in OT, where sub-second response times are often critical for real-time control systems. An industrial safety system cannot tolerate delays during an emergency.
- Account Lockouts: An IT-centric policy that automatically locks accounts after a few failed login attempts could prevent an operator from accessing a critical system during an emergency or scheduled maintenance, leading to hazardous situations or significant production losses.
- Network Dependencies: IT IAM often relies on constant network connectivity to a centralized identity provider. If this connection is lost in an OT environment, critical systems might become inaccessible, leading to a facility-wide shutdown or individual pieces of equipment operating independently but without proper control.
- System Crashes from Overload: Attempting to force modern, resource-intensive IAM agents onto legacy OT devices with limited processing power and memory can lead to system instability or crashes.
Increased Security Risks
While the intention is to improve security, an ill-conceived IT IAM implementation in OT can inadvertently create new vulnerabilities and exacerbate existing ones.
Unintended Security Consequences
- Bypassed Security Controls: If security measures are too cumbersome or disruptive, operators may find unauthorized workarounds, such as writing down passwords or using shared accounts, in an effort to maintain operations. This undermines the very purpose of IAM.
- Attack Surface Expansion: Introducing new, complex IAM infrastructure that isn’t native to OT systems can sometimes introduce new attack vectors if not properly secured and integrated.
- Lack of Visibility: A fragmented approach, where IT IAM is used for some systems and native, manual controls for others, creates blind spots and makes it difficult to get a complete picture of access across the OT environment.
- Compromised Identities: Identity-based attacks are a major threat vector, and applying inappropriate IAM strategies can make OT environments even more susceptible.
Compliance Headaches and Audit Failures
Organizations are increasingly facing stringent regulatory requirements for securing their critical infrastructure. A mismatched IAM strategy can lead to compliance failures.
Regulatory and Auditing Challenges
- Inability to Prove Access Control: Without a cohesive and auditable IAM system, it becomes challenging to demonstrate adherence to industry standards (e.g., ISA/IEC 62443, NIST) and regulatory mandates related to who can access what in OT systems.
- Ineffective Auditing: Manual access control processes and fragmented systems make it difficult to conduct thorough and accurate audits of user activity and access privileges, potentially leading to findings of non-compliance.
- Lack of Consistency: Inconsistent application of access policies due to disparate systems can result in auditing discrepancies and a perception of weak security governance.
Architectural Mismatches
The fundamental architectural differences between IT and OT systems mean that IAM solutions designed for one may simply not fit the other.
Fundamental Incompatibilities
- Protocol Differences: IT IAM often relies on protocols like Kerberos, SAML, or OAuth, which are rarely supported natively by legacy OT devices.
- Hardware Limitations: As mentioned, the computational constraints of many OT devices preclude the use of modern IAM software.
- Real-time Requirements: The deterministic and real-time nature of OT systems is incompatible with the potentially variable response times of external IAM services.
- Air-Gapped Realities: For air-gapped systems, network-dependent IT IAM solutions are entirely irrelevant.
In essence, attempting to force a square peg (IT IAM) into a round hole (OT IAM) not only fails to solve the access management problem but can also introduce new, complex challenges, jeopardizing the very operations it seeks to protect. This highlights the critical need for an IAM strategy specifically tailored to the unique demands of OT environments.
Building an OT IAM Strategy: A Risk-Based, Vendor-Aware, and Safety-First Approach
Securing OT environments with appropriate Identity and Access Management requires a nuanced and specialized approach that acknowledges their unique operational constraints and inherent complexities. A successful OT IAM strategy must be explicitly risk-based, vendor-aware, and safety-first, moving beyond the simple application of IT models.
Prioritizing Risk and Impact Analysis
The foundation of any robust OT IAM strategy is a thorough understanding of the specific risks present in the environment and the potential impact of an access control failure.
Steps for Risk-Based Assessment
- Identify Critical Assets: Pinpoint the most critical OT systems, devices, and data whose compromise would have the most severe impact on safety, production, and environmental health.
- Threat Modeling: Analyze potential threat vectors specific to each OT asset, including internal threats (e.g., insider misuse) and external threats (e.g., cyberattacks targeting vulnerabilities).
- Vulnerability Assessment: Identify weaknesses in existing access controls, legacy systems, and network configurations that could be exploited.
- Impact Assessment: Quantify the potential consequences of an access control failure, considering safety incidents, environmental damage, production downtime, financial losses, and reputational harm.
- Tiered Approach: Categorize OT systems based on their criticality and risk profile. Implement more stringent and custom-tailored IAM controls for higher-risk assets, while potentially adopting simpler solutions for less critical ones. This allows for the allocation of resources where they are most needed.
Embracing Vendor-Aware Solutions
Given the pervasive multi-vendor landscape in OT, an effective IAM strategy must be acutely aware of and designed to accommodate the distinct characteristics of each vendor’s systems.
Strategies for Multi-Vendor Environments
- Deep Vendor Integration Knowledge: Develop expertise in the specific access models, protocols, and limitations of each major OT vendor present in the environment (e.g., GE, Fujitsu, Siemens, Rockwell).
- Vendor-Specific IAM Tools: Explore IAM solutions that offer native integration or connectors for specific OT vendor platforms or which can adapt to proprietary interfaces.
- Middleware and Protocol Converters: Utilize middleware solutions or protocol converters to translate between modern IAM standards and legacy OT protocols where direct integration is not possible.
- APIs for Connectivity: Leverage any available APIs provided by newer OT systems for better integration with a broader IAM framework.
- Focus on OT-Specific IAM Solutions: Increasingly, specialized Industrial IAM (IIAM) solutions are emerging that are designed from the ground up to address the unique challenges of OT, including multi-vendor support and legacy system compatibility.
Prioritizing Safety and Availability Above All Else
The non-negotiable imperative in OT is maintaining safety and operational continuity. IAM solutions must be designed and implemented with this at the forefront.
Safety-First Design Principles
- Graceful Degradation: IAM systems must be designed to fail gracefully, ensuring that operations can continue even if the IAM service experiences an outage. This might mean allowing cached credentials for a period or having designated emergency access pathways.
- Emergency Access Procedures: Establish clear, well-documented, and regularly practiced emergency access procedures for critical systems that can bypass normal authentication mechanisms when safety or critical operations are at stake. These procedures must be securely managed and audited retrospectively.
- Minimal Authentication Friction: Where possible, minimize authentication steps and delays, especially for systems requiring immediate operator intervention. This does not mean abandoning authentication but finding less intrusive methods.
- Offline Capabilities: For systems that may operate in environments with intermittent or no network connectivity, IAM solutions must support offline authentication and access control.
- Non-Intrusive Monitoring: Implement non-intrusive monitoring of access and activity rather than relying on active authentication mechanisms that could disrupt operations.
Understanding OT Cyber Attack Vectors
Knowing how OT systems are attacked informs the defense strategy, particularly concerning identity.
Common Attack Methods Relevant to IAM
- Credential Theft: Attackers often target shared accounts, weak passwords, or default credentials to gain initial access to OT networks.
- Privilege Escalation: Once inside, attackers seek to elevate their privileges to gain control over critical processes.
- Supply Chain Attacks: Access through third-party vendors or compromised supply chain components is a growing concern, making vendor access management a critical IAM component.
Core Components of an OT IAM Strategy
While the approach is different, the fundamental pillars of IAM still apply, but with OT-specific adaptations.
Adapting the Four Pillars of IAM for OT
- Identity Lifecycle Management (ILM):
- Automated where possible, manual where necessary: Automate user creation and termination for newer, compatible OT systems. For legacy systems, establish robust manual processes with clear workflows and regular audits.
- Contractor and Third-Party Management: Implement strict procedures for managing temporary identities and access for contractors, vendors, and service providers, often requiring secure remote access solutions.
- Identity Governance: Regularly review and recertify access rights, especially for privileged accounts and shared credentials, to ensure they remain appropriate.
- Access Control (AC):
- Granular Role-Based Access Control (RBAC): Define roles that precisely map to operational responsibilities within OT, ensuring least privilege is applied meticulously.
- Attribute-Based Access Control (ABAC): Where feasible, use attributes like time of day, location, or device health to make more dynamic access decisions.
- Network Segmentation: Reinforce existing network segmentation with identity-aware access controls, ensuring that authenticated users can only access the specific segments and devices relevant to their role.
- Zero Trust for OT: Apply Zero Trust principles across OT networks, treating all access attempts as untrusted, regardless of origin. This includes identity-based access controls for plant-floor systems.
- Authentication and Authorization (AA):
- Context-Aware Authentication: Implement authentication mechanisms that consider the context of the access request (e.g., what device is being accessed, from where, and at what time) to minimize friction while maximizing security.
- Stronger, Non-Disruptive Authentication: Explore alternatives to traditional MFA, such as hardware tokens, biometrics, or device certificates, that offer strong authentication without impeding real-time operations. This includes replacing shared local accounts with individual user accounts where possible.
- Hardened Local Accounts: For systems that cannot integrate with a centralized IAM, secure local accounts with strong, unique passwords that are regularly audited, and tightly controlled.
- Privileged Access Management (PAM): Implement PAM solutions specifically designed for OT to manage and monitor access to highly sensitive systems and privileged accounts, including shared and administrative accounts. This often involves secure credential vaults and session recording.
- Identity Governance (IG):
- Regular Access Reviews: Conduct periodic reviews of all user access privileges to ensure they are still appropriate and necessary. This is crucial for reducing orphaned accounts and excessive privileges.
- Comprehensive Auditing and Logging: Implement robust logging of all access attempts and activities within OT systems. This data is critical for incident response, forensic analysis, and compliance reporting.
- Policy Enforcement: Develop clear, concise, and enforceable policies for OT identity and access, which are communicated to all personnel.
- Unified Security Strategy: Work towards a unified security model that covers both IT and OT environments, harmonizing policies and processes where possible.
The Role of Standards and Best Practices
While direct application of IT standards fails, standards like ISA/IEC 62443 and NIST provide a framework, even if they sometimes lack OT-specific implementation details for IAM. Organizations should reference these to build a structured approach.
Phased Implementation
Given the complexity and criticality of OT environments, implementing a new IAM strategy should always be a phased approach, starting with non-critical systems or in test environments, and gradually rolling out to production after thorough testing and validation. This minimizes risk and allows for continuous learning and refinement.
Ultimately, an effective OT IAM strategy is not about fitting OT into an IT mold, but about designing bespoke solutions that respect the operational imperatives of industrial control systems while significantly enhancing their security posture.
Future Trends and The Evolving Landscape of OT IAM
The world of Operational Technology is not static. The increasing convergence of IT and OT, the rise of industrial IoT (IIoT), and the continuous evolution of cyber threats are driving significant changes in how IAM is approached in industrial environments. Understanding these trends is crucial for developing future-proof OT IAM strategies.
IT/OT Convergence and Unified Security
The historical separation between IT and OT is rapidly diminishing. Manufacturers are increasingly connecting plant floor systems with business systems to leverage real-time data, improve efficiency, and enable advanced analytics.
Implications for IAM
- Unified Security Models: The convergence necessitates a unified security strategy that transcends the traditional IT/OT divide. This means establishing a single security framework and set of policies that apply across both domains, rather than managing two separate security postures.
- Seamless Data Flow with Identity: As data flows more extensively between IT and OT, identity validation will become critical for ensuring that data access and manipulation are performed by authorized entities, regardless of whether the data originates from an IT server or an OT sensor.
- Shared Identity Infrastructure (with caveats): While a fully unified identity infrastructure might be challenging due to legacy OT, there will be increasing pressure to share identity information between IT and OT for centralized management where appropriate and safe.
- Bridging the Cultural Divide: IT/OT convergence is not just a technology project; it’s an organizational shift requiring alignment across people, processes, and platforms. This includes fostering collaboration between IT and OT teams on IAM strategy and implementation.
Industrial Internet of Things (IIoT) and Edge Devices
The proliferation of IIoT devices and sensors at the edge of OT networks introduces a new layer of identity management challenges. These devices often have limited resources, operate autonomously, and generate vast amounts of data.
IAM for IIoT
- Device Identity: Beyond human users, establishing and managing the identities of millions of connected IIoT devices becomes paramount. This includes secure device onboarding, unique device identifiers, and certificates.
- Machine-to-Machine (M2M) Authentication: Securely authenticating and authorizing communication between IIoT devices, edge gateways, and cloud platforms is a crucial aspect of IIoT IAM.
- Scalability: Traditional IAM solutions may struggle to scale to the sheer number of identities introduced by IIoT, requiring specialized, lightweight, and automated approaches.
- Edge Computing IAM: As more processing moves to the edge, IAM capabilities will need to be distributed to these edge nodes to enable local authentication and authorization, even with intermittent cloud connectivity.
Artificial Intelligence (AI) and Machine Learning (ML) in IAM
AI and ML are poised to play an increasingly significant role in enhancing the capabilities of OT IAM, particularly in areas like anomaly detection and automated decision-making.
AI-Driven IAM Enhancements
- Behavioral Analytics: AI can analyze user and device behavior patterns to detect anomalies indicative of compromised credentials or insider threats. For example, an operator logging in from an unusual location or accessing systems outside their typical hours could trigger an alert.
- Automated Access Reviews: ML can assist in automating the process of reviewing and certifying access rights by identifying stale accounts or excessive privileges.
- Threat Prediction: AI can help predict potential identity-related threats by analyzing vast datasets of security events and threat intelligence.
- Dynamic Access Control: In the future, AI could enable more dynamic and context-aware access control decisions, granting or revoking access in real-time based on a complex evaluation of trust factors.
- New Risks: While AI offers significant potential, it also introduces new risks, such as overreliance or opaque decision-making in mission-critical systems, which must be carefully managed.
Zero Trust and Microsegmentation
The concept of Zero Trust, which dictates “never trust, always verify,” is gaining significant traction in OT environments as a foundational security principle.
Evolving Security Architectures
- Identity as the New Perimeter: With Zero Trust, the focus shifts from network perimeters to individual identities. Every user and device, whether on the IT or OT side, must be authenticated and authorized.
- Microsegmentation with Identity: Microsegmentation, the practice of isolating network workloads from each other, when combined with identity-centric controls, allows for extremely granular access policies, ensuring that even if an attacker breaches one segment, their movement is severely restricted.
- Continuous Verification: Zero Trust requires continuous verification of identities and their access privileges, rather than a one-time check. This aligns well with the need for vigilant security in OT.
Secure Remote Access
The increasing need for remote monitoring, maintenance, and support for OT systems, particularly post-pandemic, has highlighted the importance of secure remote access solutions.
Key Enhancements for Remote Access
- Identity-Centric Remote Access: Remote access solutions for OT must be identity-centric, ensuring that only authorized individuals and devices can establish connections.
- Privileged Access Management (PAM) for Remote Vendors: Robust PAM for external vendors and contractors accessing OT systems remotely is critical, including session recording and just-in-time access.
- VPN Replacement: Traditional VPNs are often inadequate for OT remote access due to their broad network access. Modern solutions focus on granular, identity-driven access to specific devices or applications.
The future of OT IAM governance is dynamic and complex, demanding continuous adaptation and innovation. Organizations that proactively address these evolving trends with tailored strategies will be better positioned to secure their critical industrial assets and ensure operational resilience.
Challenges in Implementing OT IAM Governance
Despite the clear need for specialized OT IAM, organizations face numerous hurdles in its implementation. These challenges stem from a combination of technical limitations, organizational dynamics, and the inherent nature of industrial operations.
Technical Debt and Legacy Systems
The pervasive presence of highly specialized and often antiquated equipment is perhaps the single biggest technical impediment to robust IAM in OT.
The Weight of the Past
- Unpatchable Vulnerabilities: Many legacy OT systems run on outdated operating systems or firmware that no longer receive security updates, leaving them perpetually vulnerable. Applying modern authentication protocols or installing agents on these systems is often impossible.
- Proprietary Interfaces: The lack of open standards means that each vendor’s system may require custom integration work, which can be expensive, time-consuming, and difficult to maintain as systems evolve.
- Limited Computation Power: As discussed, the reduced processing power and memory of older devices prevent the use of sophisticated security agents or encryption.
- Disruption Risk During Modernization: Modernizing legacy OT without disrupting production is a critical challenge requiring careful planning and execution.
Operational Constraints and the “Don’t Touch What Works” Mentality
The paramount importance of uptime and safety fosters a strong cultural resistance to changes that could introduce instability.
Cultural and Operational Roadblocks
- Fear of Downtime: Even minor changes to critical operational systems can be perceived as too risky, leading to a “don’t touch what works” mentality. The cost of an outage in OT can be astronomical, both financially and in terms of safety.
- Real-time Demands: The deterministic nature of many OT processes means that any security measure that introduces latency or variability in response times is a non-starter.
- Skill Gaps: OT engineers, while experts in their domain, may lack specialized cybersecurity knowledge, particularly concerning identity management principles. Conversely, IT security professionals may not fully grasp the operational nuances and safety requirements of OT.
- Difficulty in Testing: Testing IAM changes in a live OT environment is highly risky. Setting up realistic testbeds that accurately mimic the production environment can be prohibitively expensive and complex.
Organizational Silos and Lack of Collaboration
Historically, IT and OT teams have operated independently, with distinct objectives, reporting structures, and budgets. This organizational divide often hinders effective OT IAM implementation.
Bridging the Organizational Gap
- Conflicting Priorities: IT typically prioritizes confidentiality and data integrity, while OT focuses on safety, availability, and process integrity. These differing priorities can lead to friction when trying to implement a unified IAM strategy.
- Lack of Communication and Understanding: Poor communication between IT and OT teams can lead to misaligned strategies, missed requirements, and a lack of buy-in for IAM initiatives.
- Budget Allocation: Securing funding for OT IAM can be challenging as organizations may not yet fully appreciate its unique complexities and requirements compared to IT.
Regulatory and Compliance Ambiguity
While there are increasing mandates for securing critical infrastructure, specific guidance for OT IAM is still evolving.
Navigating the Regulatory Landscape
- Evolving Standards: While frameworks like ISA/IEC 62443 and NIST exist, their application to the specific nuances of IAM within OT can be challenging and often requires interpretation.
- Audit Preparedness: Organizations struggle to demonstrate compliance with access control requirements when their OT IAM systems are fragmented and rely on manual processes.
Managing Third-Party Access
The increasing reliance on external vendors, contractors, and service providers for specialized OT maintenance and support introduces significant IAM challenges.
Securing External Access
- Uncontrolled Remote Access: Providing remote access to OT systems for third parties without robust IAM can create major vulnerabilities.
- Vendor-Owned Devices: Managing identity and access for devices brought onto the plant floor by vendors can be complex.
- Lack of Visibility: It’s often difficult to monitor and audit the activities of third-party users once they gain access to OT systems.
Addressing these implementation challenges requires strong leadership, cross-functional collaboration, a phased approach, and a deep understanding of both cybersecurity principles and OT operational realities.
Case Studies and Real-World Implications
To fully grasp the critical importance of a specialized OT IAM strategy, it’s beneficial to examine real-world scenarios and the implications of both successful and unsuccessful approaches. While specific company names may be withheld for security reasons, these examples highlight common patterns.
Case Study 1: The Outdated System and Shared Credentials
Scenario: A mid-sized manufacturing plant relies on a legacy PLC system from the 1990s, critical for controlling a key production line. This system was not designed for individual user accounts; all operators share a single, hardcoded password. The password has not been changed in over a decade. The PLC system is connected to a small, isolated network segment.
IT IAM Misapplication: An IT security audit recommends implementing MFA and regular password rotations for the PLC system, treating it like a standard IT application login.
Resulting Problems:
- Operational Disruption: Attempts to modify the PLC’s authentication mechanism directly (if even possible) were met with warnings from the vendor about potential firmware corruption and process instability.
- Resistance from OT: Operators strongly resisted password changes, citing the need for immediate access during critical production phases and fear of forgetting a new password causing downtime.
- Increased Risk: When IT pushed for a solution, the OT team eventually implemented a shared “emergency password” on a sticky note, completely circumventing security and creating an even greater vulnerability.
Corrective OT IAM Approach: Instead of direct authentication modification, the plant implemented a Privileged Access Management (PAM) solution for OT. This involved:
- Placing the PLC behind a secure jump server.
- Requiring operators to authenticate individually to the jump server using their unique IT credentials and MFA.
- The PAM system then automatically injected the hardcoded PLC password, abstracting it from the users.
- Session recording and auditing of all PLC access via the jump server were enabled.
- Physical security around the PLC console was enhanced, along with continuous network monitoring of the segment for anomalous activity from other sources.
Outcome: Improved security posture without impacting operations or requiring direct modification of the sensitive legacy PLC. Full audit trail of who accessed the PLC and when.
Case Study 2: Remote Vendor Access to SCADA Systems
Scenario: A utility company relies on an external vendor to service their SCADA systems for water treatment facilities. The vendor traditionally used a direct VPN connection to the utility’s OT network, giving them broad access. The VPN credentials were static and shared among vendor technicians.
IT IAM Misapplication: The IT department’s policy was to issue VPN tokens with complex passwords and require monthly password changes.
Resulting Problems:
- Unacceptable Delays: Vendor technicians found the frequent VPN password changes cumbersome, and when a critical SCADA component failed, the technician struggled with login, delaying emergency response.
- Broad Network Exposure: Even with VPN, the vendor had unfettered network access to a large portion of the OT network, posing a significant lateral movement risk if their endpoint was compromised.
- Accountability Gap: With shared static VPN credentials, it was impossible to pinpoint which specific technician performed an action on the SCADA system, hindering incident investigation.
Corrective OT IAM Approach: The utility implemented an OT-specific Secure Remote Access solution featuring:
- Zero Trust Architecture: No implied trust for any remote connection.
- Granular Access: Vendor technicians could only initiate connections to the specific SCADA components they were authorized to service, not the entire network.
- Just-in-Time Provisioning: Access was granted only for the duration of the scheduled maintenance window.
- Individualized Identities: Each technician used their strong, unique credentials (with MFA) to access the remote access gateway.
- Session Recording and Monitoring: All remote user sessions, including keystrorokes and screen activity, were recorded and monitored for auditability and rapid incident response.
Outcome: Significantly reduced attack surface for remote access, enhanced accountability, and improved incident response capabilities without hindering the vendor’s ability to perform necessary services effectively.
Case Study 3: The Connected Industrial Robot and IIoT
Scenario: A large automotive manufacturer deployed a fleet of new industrial robots, part of an IIoT initiative. These robots regularly communicate with a central control server and cloud analytics platform. Initially, the robots were configured with default vendor credentials for cloud access.
IT IAM Misapplication: The IT team assumed the manufacturer’s existing enterprise SSO solution could manage the robots’ identities.
Resulting Problems:
- Incompatibility: The robots’ embedded operating systems and communication protocols were incompatible with the enterprise SSO system (e.g., no browser for web-based authentication).
- Credential Sprawl: Each robot had its own set of default credentials for various services, creating a management nightmare and a significant security risk if these defaults were not changed.
- No Central Visibility: There was no centralized way to onboard, monitor, or revoke access for individual robots, making it hard to manage their lifecycle.
Corrective OT IAM Approach: The manufacturer implemented a Device Identity and M2M Authentication platform specifically designed for IIoT:
- Hardened Device Identities: Each robot was provisioned with a unique, cryptographically strong identity (e.g., X.509 certificate) at the factory or during commissioning.
- Automated Enrollment: A secure enrollment process automatically registered the robot’s identity with the central management platform.
- M2M Mutual TLS: Robots and the central server mutually authenticated using certificates before establishing communication (Mutual TLS), ensuring only trusted devices could interact.
- Centralized Policy Management: Access policies for what data each robot could transmit or receive were centrally managed and enforced.
- Automated Credential Rotation: Certificates were automatically rotated on a regular schedule, eliminating static default credentials.
Outcome: Secure, scalable identity management for a large fleet of IIoT devices, supporting the goals of digital transformation while mitigating significant security risks.
These case studies underscore the critical lesson: OT IAM is not a miniature version of IT IAM. It demands a specialized understanding of industrial processes, an appreciation for legacy technologies, and an unwavering commitment to safety and uptime. Organizations must invest in tailored strategies and solutions to protect their most vital assets.
The Path Forward: Best Practices and a Call to Action
The journey towards robust OT IAM governance is multifaceted and ongoing. It demands a strategic and holistic approach that integrates technology, process, and people. By adopting a set of best practices, organizations can navigate the complexities and build a resilient security posture for their operational environments.
Key Best Practices for OT IAM Governance
- Conduct a Comprehensive Risk Assessment and Asset Inventory:
- Know Your Environment: Gain a deep understanding of all OT assets, their criticality, vulnerabilities, and interdependencies. This includes legacy equipment, network segments, and control systems.
- Prioritize Based on Risk: Focus IAM efforts on the highest-risk assets and systems first, where the impact of compromise is most significant.
- Develop a Holistic IT/OT Security Strategy:
- Unified Vision: Work towards a single, overarching security strategy that encompasses both IT and OT, acknowledging their unique characteristics while seeking commonalities for identity management.
- Cross-Functional Teams: Foster collaboration between IT and OT teams, establishing shared goals and clearly defined roles and responsibilities for IAM.
- Implement a Phased and Incremental Approach:
- Start Small, Scale Smart: Begin with pilot projects on non-critical systems or in test environments. Learn from these implementations and gradually expand to more critical areas.
- Avoid Rip-and-Replace: Work with existing infrastructure where possible, leveraging middleware and specialized OT IAM tools to integrate rather than attempting to replace perfectly functional but legacy systems.
- Embrace Zero Trust Principles for OT:
- Never Trust, Always Verify: Assume no implicit trust for any user, device, or application within the OT network. Every access attempt must be authenticated and authorized.
- Identity-Based Microsegmentation: Combine network microsegmentation with identity context to create highly granular access controls, limiting lateral movement for any compromised entity.
- Prioritize Privileged Access Management (PAM) for OT:
- Control Superuser Access: Implement robust PAM solutions to manage, monitor, and audit all privileged access to critical OT systems. This is paramount for preventing insider threats and containing external breaches.
- Eliminate Shared Accounts: Where possible, replace shared accounts with individual, auditable privileged accounts, even if managed through a PAM vault.
- Session Management: Record and monitor privileged sessions to critical OT devices for forensic analysis and compliance.
- Secure Remote Access for Vendors and Employees:
- Least Privilege Remote Access: Grant remote access only to specific devices or systems required for the task, for a limited duration (just-in-time access).
- Strong Authentication: Enforce strong, individualized multi-factor authentication for all remote users.
- Session Monitoring: Implement continuous monitoring and auditing of all remote sessions into OT environments.
- Address Legacy System Challenges Strategically:
- Protective Layers: For systems that cannot be directly integrated with modern IAM, create protective layers around them using secure gateways, jump servers, or network segmentation combined with identity-aware firewalls.
- Hardening and Audit: Continuously harden access to legacy systems through physical controls, secure configurations, and meticulous auditing of activities on those systems.
- Invest in Education and Training:
- Cross-Training: Educate both IT and OT teams on the unique security requirements and operational constraints of each other’s environments.
- User Awareness: Train all personnel (operators, engineers, maintenance staff) on the importance of OT security and their role in maintaining strong access control.
- Leverage OT-Specific IAM Solutions and Expertise:
- Specialized Tools: Explore and implement IAM solutions that are purpose-built for OT environments, designed to handle multi-vendor complexities, legacy protocols, and real-time operational demands.
- Consult with Experts: Engage with experts who possess deep knowledge of both OT and cybersecurity to guide the development and implementation of your IAM strategy.
- Establish Robust Monitoring, Auditing, and Incident Response:
- Continuous Monitoring: Implement continuous monitoring of identity-related events and access anomalies across the OT network.
- Centralized Logging: Aggregate and normalize logs from various OT systems (where possible) for better visibility and threat detection.
- Incident Response Playbooks: Develop specific incident response playbooks for identity-related incidents in OT, including procedures for compromised credentials or unauthorized access.
The Imperative of Specialized OT IAM
The distinction between IT and OT Identity and Access Management is not merely semantic; it represents a fundamental divergence in operational priorities, technological landscapes, and risk profiles. While IT benefits from a relatively standardized and automatable IAM environment, OT demands a bespoke approach that prioritizes safety, availability, and the accommodation of a complex, multi-vendor, and often legacy-laden ecosystem. Simply porting IT IAM models to industrial control systems is a recipe for disaster, potentially compromising critical infrastructure, endangering personnel, and incurring massive financial losses.
The path forward requires a deliberate, risk-based, vendor-aware, and safety-first strategy that integrates specialized technologies, fosters cross-functional collaboration, and continuously adapts to the evolving threat landscape. By investing in tailored OT IAM governance, organizations can fortify their defenses, ensure operational resilience, and securely navigate the ongoing convergence of the digital and physical worlds.
Is your organization struggling to bridge the gap between IT and OT IAM?
At IoT Worlds, we understand the intricate challenges of securing operational technology environments. Our expert consultants specialize in designing and implementing robust, safety-first Identity and Access Management strategies tailored to the unique demands of your industrial systems. From legacy integration to Zero Trust architectures, we help you protect your critical assets without compromising operations.
Don’t let the complexities of OT IAM leave your vital infrastructure vulnerable.
Contact us today to discuss how we can help you build an impenetrable defense for your industrial operations. Send an email to info@iotworlds.com.