You need to create a high-availability cluster if you want edge IoT. This article will cover Scalability, Security and Open Architecture. Next, you will learn how to set up your cluster for edge IoT deployments. This article will show you how to create your own edge IoT cluster in your datacenter or cloud.
A high-availability cluster for edge iot
It is important to think about the use cases you wish to implement in order to ensure high availability. It is important to consider the goals and objectives of your project as well as the operational cost and productivity impact of downtime. Consider the single point of failure you will face if your IoT infrastructure goes down. Most cases, reducing recovery time will lead to increased complexity and higher costs.
A cluster is a great option for edge computing. It allows you to scale up and process more data at your edge, without having it sent to the cloud. A cluster helps you to maintain regulatory compliance as well as data residency. Edge clusters can be highly available due to failback options, and the ability of adding new nodes to replace a failed node. A cluster configured for high availability is best if you are concerned about security.
You can prevent this by using hardware redundancy and creating a high-availability cluster. You can avoid costly downtime by avoiding single points of failure. The cluster is resilient and there are very low chances that one of its nodes will go down. Your cluster will never fail if it has high availability.
Cluster computing is a new paradigm. Single Board Computers have made cluster computing possible for automobiles and mobile devices. Cluster computing offers many benefits, including lower costs, higher data security, and greater system reliability. Cluster computing was once limited to cloud computing. However, single-board computers have made it possible to configure a new generation small computer hardware to create clusters of up to four Jetson nano modules.
Security
For the next generation IoT devices security measures are essential. Small, affordable sensors are no exception. Even the most effective security measures can fail if the components of the device become compromised and the software cannot be updated. Hardware is the best security solution for devices. ReSIoT is a reconfigurable security framework that was created by the IEEE team. People will be more concerned about protecting their data as the world becomes more connected.
The edge-based system reduces the network attack surface, in addition to the physical device. Traffic to and from IoT devices and edge traverses fewer hops, which reduces the chance of data manipulation or unauthorized access. Edge-iot security protects data at all points, from at rest to in transit and during use. This helps prevent cyberattacks and preserve data integrity. Any security breach can lead to serious consequences.
Different types of attacks can be applied to an IoT Edge device. OEMs need to understand how to best protect these devices. Many edge devices have native security features such as encryption and cryptography, in addition to security software. They can also be configured to control or allow data access. There is still much to be done. Edge security shouldn’t be an afterthought. It should be part of the overall security strategy.
Edge computing is now a common solution due to the widespread adoption of IoT technology. Edge security solutions allow businesses to be responsive in real time and store transient data in a cost-effective manner. It can be difficult to secure IoT devices. It is essential to manage edge security effectively. A robust solution should also be capable of addressing the offline operations. IoT security is critical, regardless of whether you use the device to communicate with other networks and/or to monitor your devices’ status.
The key component of the overall IoT strategy is to manage the security of Azure IoT edge devices. The Azure IoT Edge security framework is designed to provide flexibility while providing protection. Security solutions should be simple to implement and easy to examine. They can be trusted just as much as the cloud. An Azure IoT Edge device should use secure hardware to ensure security.
Scalability
The Internet of Things (IoT), which is rapidly growing, has a greater workload than ever before. Edge servers are limited in their ability to handle multiple requests simultaneously, which makes them unable to manage the concurrent workload. High-volume IoT systems can scale up if edge servers are capable of handling multiple simultaneous requests. Edge servers can also be more expensive in terms of energy and latency.
In 2025, 30% will be live-streamed, which means that there won’t be a delay of two seconds between input and action. This means that 30% of all scenarios require edge resources. We need to find new ways of approaching edge computing in order to reach that goal. We must first understand the basics of edge computing. It is important to understand what makes edge computing different from data centres.
Edge computing is a way to address these problems by moving processing, storage and communications to the edge. This architecture aims to reduce overhead computations and increase the battery life of resource-constrained IoT gadgets. Edge servers can scale to accommodate both delay-sensitive or delay-tolerant applications. We must also consider scaling edge servers. IoT systems can be scaled to meet increasing requests by using energy-efficient resources.
Edge computing also has to overcome the latency in communications between edge devices, the Cloud, and other devices. Edge computing solutions need to balance latency in transmission and latency in computing, and decide the best offloading scheme. Vertical scaling architectures allow for small resources to be strategically placed at edge locations. This architecture allows small-scale computing capabilities. It minimizes transmission latency and ensures the highest availability. Although the results are impressive, there are still some challenges.
Although edge IoT systems have clear benefits, IoT deployments are often unsuccessful. These deployments can involve many components such as new carrier agreements, regional certifications and acquiring certifications. Because it prevents project failures, which can be as high as 75 percent, scaling is crucial in the IoT. IoT developers need to look for providers who have experience in specific use cases.
Open architecture
You need an open architecture to address the most pressing issues of this rapidly growing industry, whether you are building a system for Internet of Things applications or expanding your existing network. Edge architecture offers the features necessary to solve these problems and ensure privacy protection as well as responsiveness in real-time. With computing power increasing, data storage has increased and processing is closer to users and devices.
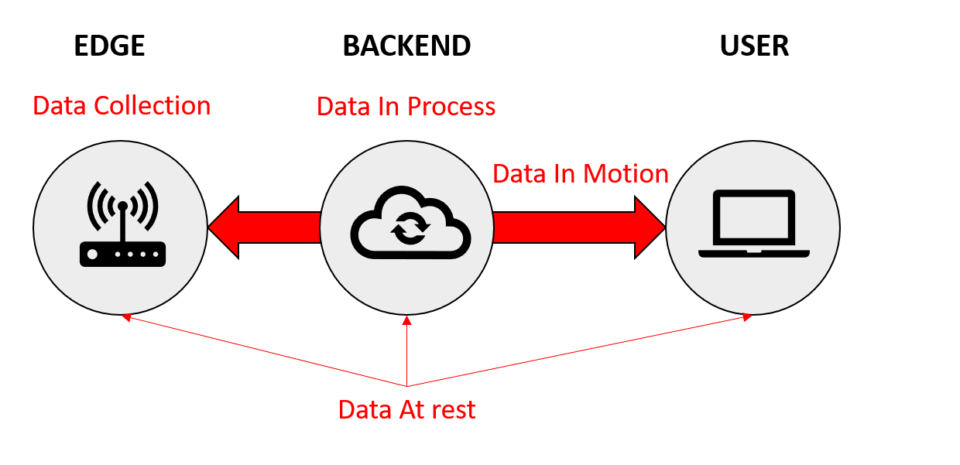
Edge IoT computing systems consist of two layers: physical and network. The physical layer is made up of sensors, actuators and connected devices. Edge devices are connected to each other in order to transmit data to the internet. The network layer is responsible for data transmission in the case of networked edge devices. After the network layer has been established, data is distributed to all devices. This data can then be used to improve service quality.
The gateway is also part of the architecture. Edge computing can be enabled. It acts as the communication hub for an IoT network, and performs crucial functions such as processing sensor protocols and translating them. Once the data has been collected, it can be routed to either the cloud or an on-premises network. Edge computing allows you to increase performance, reliability, security, and efficiency by leveraging data in this way. The device is able to process data at high speed and sync it with the cloud, providing ultimate storage.
Several open standards enable edge computing. Osmotic Computing, for example, uses micro virtual machines that move data from the local level to the cloud. This is similar to Dew computing, which stores data locally on the user’s device. Dew Computing is dependent on a data synchronization protocol. It generates significant traffic, particularly for multimedia data. These are just some examples of edge computing that is growing in popularity in the ioT environment.
Edge computing offers a better operational efficiency. Edge computing also lowers latency and bandwidth, while allowing high-use applications. It also allows new processing technologies such as machine learning and artificial Intelligence to be used in the IoT network. Edge computing is not for all organizations. Organizations without the proper IoT infrastructure may face security risks and additional risks.